Additional Tasks
Connect Visualizer to Quantum Fabric on Azure
For details about connecting to Quantum Fabric Console through Visualizer, refer to Connecting to Quantum Fabric.
Multiple Node Pools in Azure Kubernetes Service
In Azure Kubernetes Service (AKS), nodes that have the same configuration are grouped into node pools, which contain virtual machines that run your apps. To support apps that have different computing or storage requirements, you can use multiple node pools in a single cluster. This feature enables higher control over how you can create and manage multiple node pools.
Currently, the Fabric installation uses an AKS cluster with a single node pool to deploy applications. This single node pool contains all the application components such as identity, integration, console, kpns, and the api portal. For multiple environments, Fabric creates multiple AKS clusters with all the resources.
To optimize the effort of operating and maintaining multiple clusters, Fabric on Azure now uses the multi node pool architecture. In this architecture, multiple node pools are created in a single AKS Cluster. This AKS cluster contains a node pool named Shared, which contains components that are shared by all environments, such as console, identity, and the api portal. In addition to the shared components, every node pool in the cluster contains the kpns and integration components. An Ingress controller is configured to implement host-based routing to the respective node pool.
Update the Azure Kubernetes Service Cluster configuration
You must have the current config files to update the AKS cluster configuration.
After the installation is complete, take a backup of the unzipped directory where you installed the kony-fabric-containers-azure.zip file to perform further updates to the AKS clusters.
IMPORTANT: If you do not have a backup of the unzipped directory, the AKS cluster might not update properly.
Set up Azure Content Delivery Network (CDN)
A Content Delivery Network (CDN) is a distributed network of servers that can efficiently deliver web content to users. To minimize latency, CDNs store cached content on edge servers in Point-Of-Presence (POP) locations that are close to end users.
The Azure Content Delivery Network (CDN) offers a global solution for developers to rapidly deliver high-bandwidth content to users by caching the content at strategically placed physical nodes across the world.
NOTE: The Azure CDN SKU for AKS cluster is set to Premium Verizon, which supports configuration of cache rules for Quantum Fabric Apps.
- In the properties file (
trail.propertiesorenterprise.properties), set the value of theAZURE_CDN_ENABLEDproperty totrue.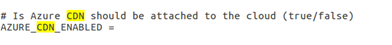
- Set the CDN Endpoint, and then follow either of these steps based on the type of cloud:
- For an SSL enabled cloud (
IS_SSL_ENABLED = true), after creating the CDN endpoint, map the CDN endpoint to a custom domain name.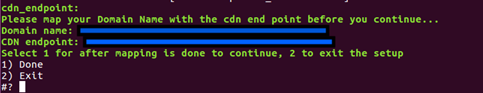
- For an SSL disabled cloud (
IS_SSL_ENABLED = false), mapping of the server domain name is not required.
- For an SSL enabled cloud (
After you create the CDN profile and endpoint, you need to manually configure the CDN settings in the Azure portal.
- Sign into the Azure portal by using your Microsoft account credentials.
- From the left navigation pane, select Resource groups. All existing resource groups appear.
- Select the resource group in which the AKS Cluster is created.
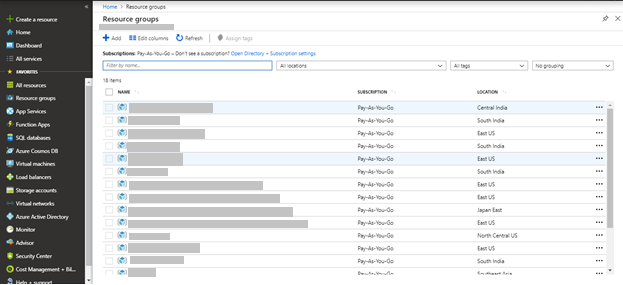
- If the cloud is SSL enabled, open CDN Endpoint from the list of resources in the Azure Resource Group.
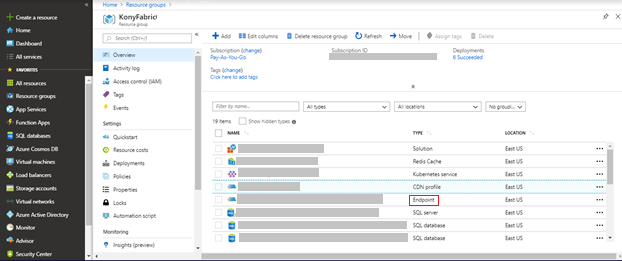
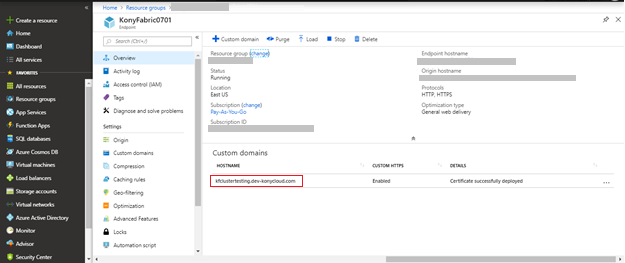
- Click Custom Domain.The Custom Domain page appears.
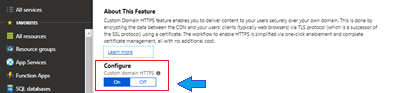
- Select ON to enable HTTPS for the custom domain.
- In the Azure Resource Group that has the created AKS cluster, from the list of resources, select CDN profile.
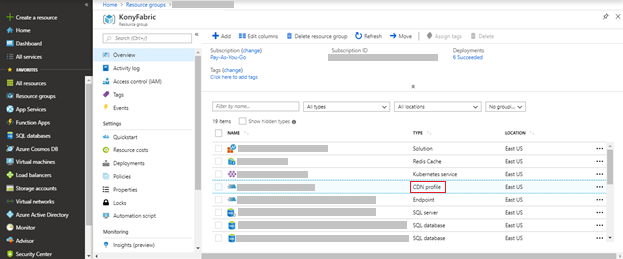
- On the top navigation bar, click Manage.
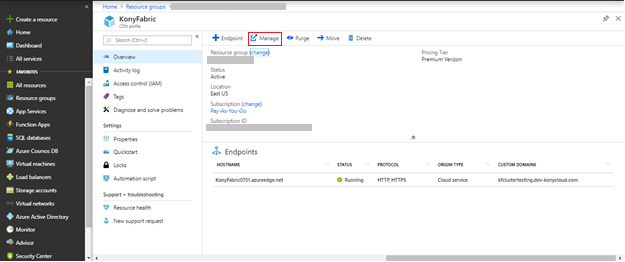
- Configure the rules in the CDN Manage Console.
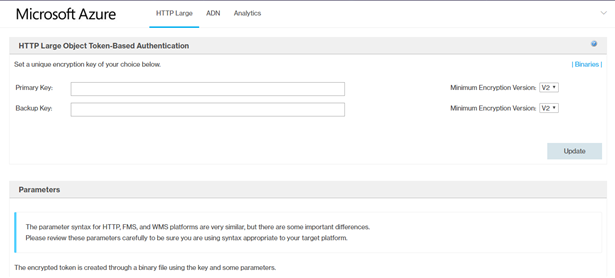
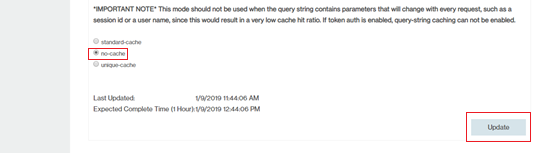
- From the HTTP Large list, select Cache settings → Query-String Caching .
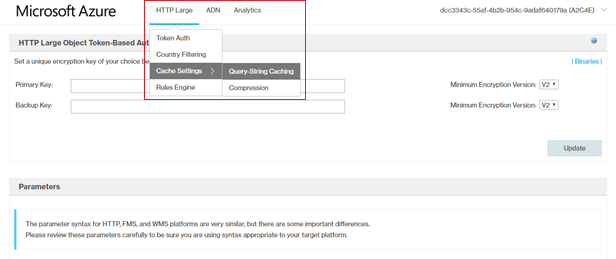
- Select no-cache, and then click Update.
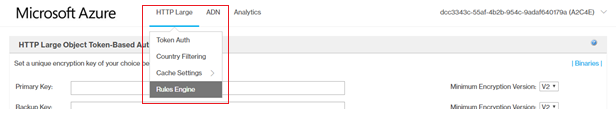
- From the HTTP Large list, select Rules Engine.
- Configure the required rules.
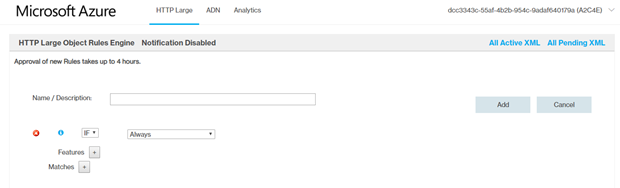
- Rule 1
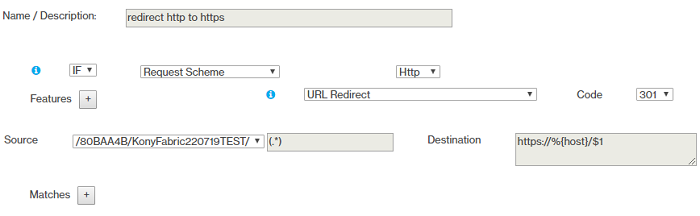
- Rule 2
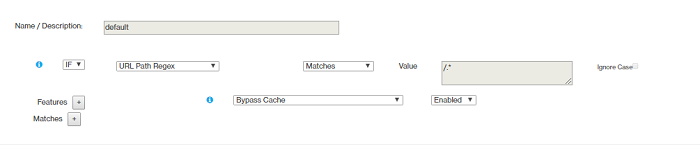
- Rule 3
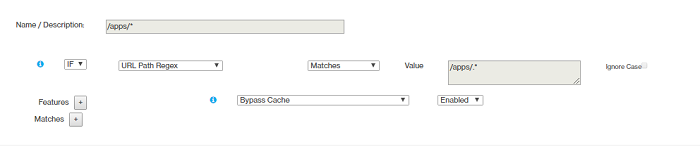
- Rule 4
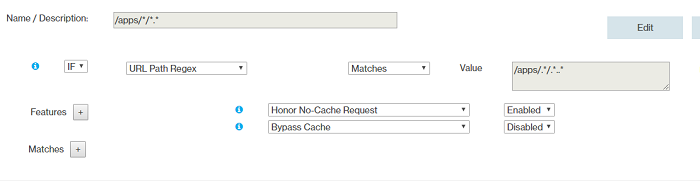
- Rule 5
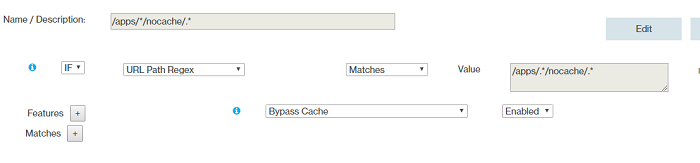
- Rule 6
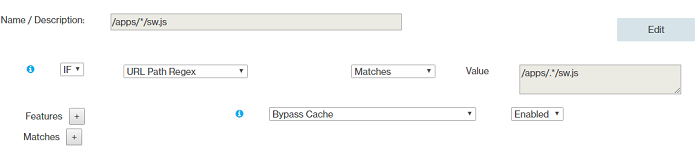
- Rule 7
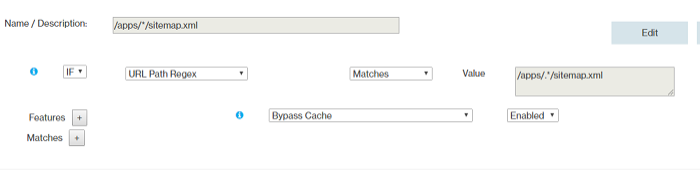
- Rule 8
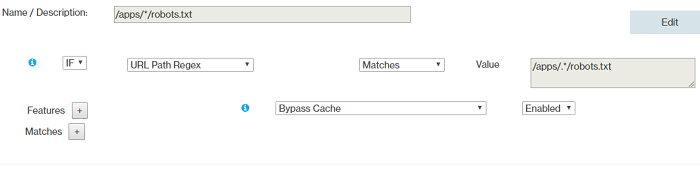
- Rule 9
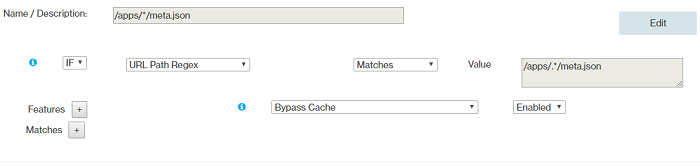
- Rules Order
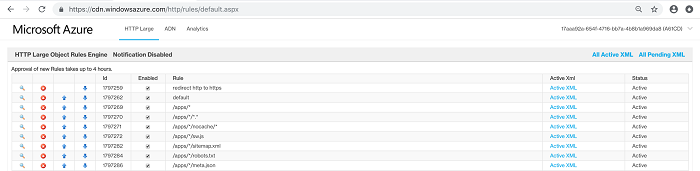
- Rule 1
Configure Clam AntiVirus for Azure Virtual Machines
Clam AntiVirus (ClamAV) is an open-source anti-virus software toolkit. You can install ClamAV on Azure Virtual Machines in the kubernetes cluster. ClamAV is an on-demand scanner, and only runs when it is invoked.
A cron job is configured to run ClamAV on Azure Virtual Machines based on the frequency specified in the properties file. ClamAV scans the files in the virtual machine and pushes the logs (clamscan.log and freshclam.log) from the /var/log/clamav directory to the clamavlogs container in the storage account of the Azure Resource Group in which the AKS cluster is created.
Provide the following inputs in the properties file to enable ClamAV.
Follow these steps to install ClamAV on your Azure Virtual Machine:
- In the properties file (
trail.propertiesorenterprise.properties), set the value of theINSTALL_CLAMAVproperty totrue. - Place the SSH private key and the SSH public key in the
sshkeysfolder with the following names:- SSH private key:
id_rsa - SSH public key:
id_rsa.pub
- SSH private key:
- Set the frequency of the cron job to start the ClamAV scan and push the generated logs to the storage account.
- You must maintain a minimum gap of 02:30 hrs. between the values of
clamscan_cron_scheduleandclamscanlogpush_cron_schedule. - All cron job timings follow the UTC timezone.
clamscan_cron_schedule and clamscanlogpush_cron_schedule in the properties file (trail.properties or enterprise.properties).* * * * * | | | | | | | | | | | | | | +---- Day of the Week (range: 1-7, 1 standing for Monday) | | | +------ Month of the Year (range: 1-12) | | +-------- Day of the Month (range: 1-31) | +---------- Hour (range: 0-23) +------------ Minute (range: 0-59) * = any value
For example, if you configure the crontab timing as 00 16 * * *, this indicates that the crontab runs every day at 16:00:00 (UTC).
Follow these steps to access the ClamAV logs in the Virtual Machine.
- Sign into Jumpbox by using the following SSH command:
ssh devops@<Jumpbox_Public_IP_Address> - Log onto the Virtual Machine from Jumpbox by using the following SSH command:
ssh -i id_rsa azureuser@<Virtual_Machine_IP_Address> - Navigate to the
/var/log/clamavdirectory by using the following command:cd /var/log/clamav
This directory contains theclamscan.logandfreshclam.logfiles that are generated by ClamAV after scanning the Virtual Machine.
Another cron job is configured to push the generated logs into the Azure Storage Account.
- View existing cron jobs on the VM by using the following command:
crontab -l
- Open the crontab list in edit mode by using the following command:
crontab -e
The freshclam.conf file configures the ClamAV Database Updater.
- Go to the
etc/clamav/directory. - Open the
freshclam.conffile in any editor to make any required changes to the configuration file.
All the logs generated by CLAMAV are pushed to the Azure Storage Account.
- Sign into the Azure portal by using your Microsoft account credentials.
- From the left navigation pane, select Resource Groups. All existing resource groups appear.
- Select the resource group in which the AKS Cluster is created.
- Select the storage account from the list of resources that are available in the resource group.
- Click Blobs. The containers available in the storage account are displayed.
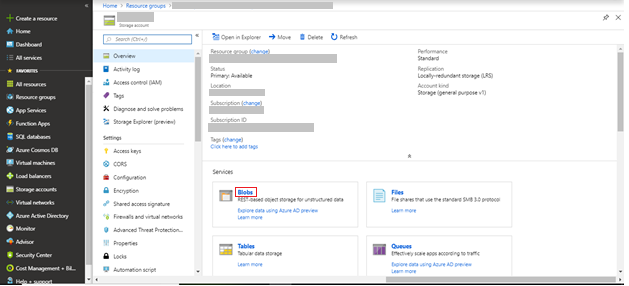
- From the list of containers that are available in the storage account, select the clamavlogs container.
The log files that are pushed by ClamAV from the virtual machine are displayed.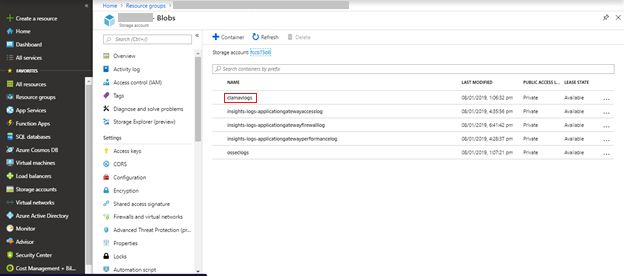
- Click Download. A zip file is downloaded to your system.
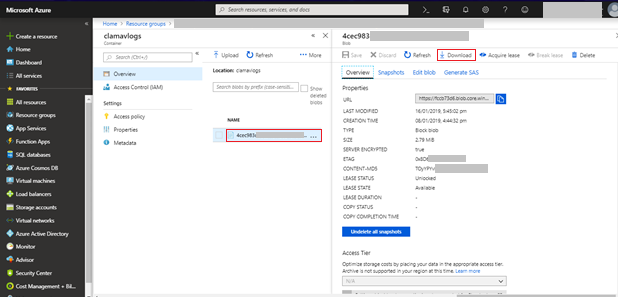
- Extract the content from the downloaded zip file. You can view all the logs that are pushed by CLAMAV from the virtual machine.
Configure OSSEC Intrusion Detection
OSSEC is an open source Host-based Intrusion Detection System (HIDS). It has a powerful correlation and analysis engine, and can perform integrating log analysis, file integrity checking, Windows registry monitoring, centralized policy enforcement, rootkit detection, real-time alerting, and active response.
OSSEC runs as a daemon process. It notifies through alert logs when intrusion attacks occur. These alert logs are pushed to the osseclogs container in the storage account in the Azure Resource Group in which AKS cluster is created.
Provide the following inputs in the properties file to enable OSSEC.
- In the properties file (
trial.propertiesorenterprise.properties), set the value of theINSTALL_OSSECflag as true.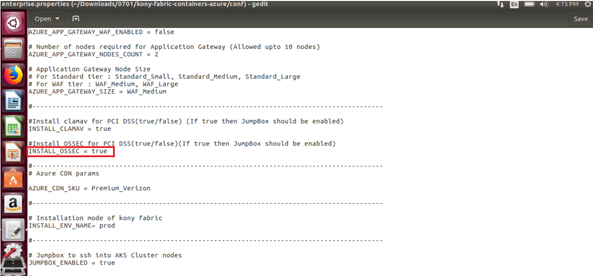
- Configure a cron job to push the alerts from the
/var/ossec/logs/alerts/alerts.logfile to the Azure Storage Account.
OSSEC is a daemon process; therefore, it continuously detects intrusion activities and stores alerts in thealerts.logfile. - You can modify the default values of the cron job based on your requirement.
- All cron job timings follow the UTC timezone.
- Place your SSH private key in the
sshkeysfolder with the nameid_rsa.
cronjob osseclogpush_cron_schedule property in the properties file (trial.properties or enterprise.properties) to set the frequency value of the cron job. Configure the Crontab timing in the following format:* * * * * | | | | | | | | | | | | | | +---- Day of the Week (range: 1-7, 1 standing for Monday) | | | +------ Month of the Year (range: 1-12) | | +-------- Day of the Month (range: 1-31) | +---------- Hour (range: 0-23) +------------ Minute (range: 0-59) * = any value
For example, if you configure the crontab timing as 00 16 * * *, this indicates that the crontab runs every day at 16:00:00 (UTC).
Follow these steps to access OSSEC logs in the Virtual Machine.
- Sign into Jumpbox by using the following command:
$ ssh devops@<Jumpbox_Public_IP_Address> - Log onto the Virtual Machine from the Jumpbox by using the following command:
$ ssh -i id_rsa azureuser@IPaddress of Virtual Machine - Sign in as a root user by using the following command:
$ sudo su - View the syslogs at
/var/log/syslogby using the following commands:$cd /var/log/$cat syslog - Logs that are created by OSSEC daemons are stored in the sub directories of
/var/ossec/logs. Follow either of these steps to view the logs or the alerts:- View the OSSEC logs at
/var/ossec/logs/ossec.logby using the following commands:$cd /var/ossec/logs/$cat ossec.log - View the OSSEC alerts at
/var/ossec/logs/alerts/alerts.logby using the following commands:$cd /var/ossec/logs/alerts/$cat alerts.log
- View the OSSEC logs at
- View the existing cron jobs by using the following command on the VM:
$ crontab -l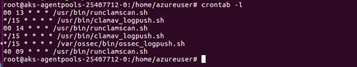
- Open the crontab list in edit mode by using the following command:
crontab -e
The logs that are generated by OSSEC are pushed to the Azure Storage Account.
- Sign into the Azure portal by using your Microsoft account credentials.
- From the left navigation pane, select Resource groups. All existing resource groups appear.
- Select the resource group in which the AKS Cluster is created.
- From the list of resources available in the resource group, select the storage account.
- Click Blobs.
The containers available in the storage account are displayed.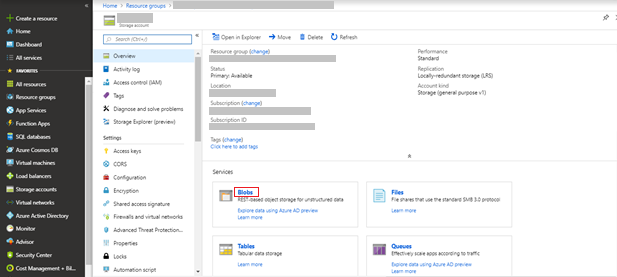
- From the list of containers that are available in the storage account, select the osseclogs container.
The log files pushed by OSSEC from the Virtual Machine are displayed.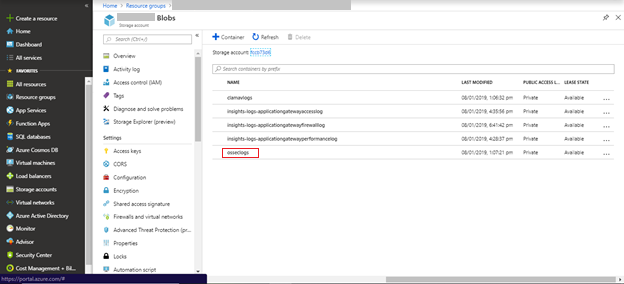
- Click Download. A zip file is downloaded to your system.
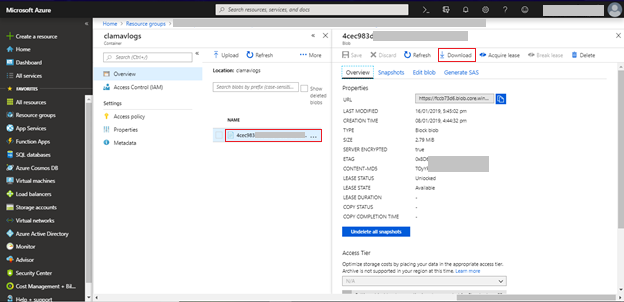
You can now view all the logs that are pushed by OSSEC from the virtual machine.
preloaded-vars.conf file to give customized inputs (other than defaults) to install OSSEC.- Sign into the specific Virtual Machine (node) by using SSH keys in the terminal.
- Navigate to the
/home/azureuser/ossec-hids-2.9.0/etc/directory by using following command:$ cd /home/azureuser/ossec-hids-2.9.0/etc/ - Open the
preloaded-vars.conffile and edit it based on your requirement.
ossec.conf file and change the existing configurations of OSSEC.- Sign into the specific Virtual Machine (node) by using SSH keys in the terminal.
- Navigate to the
/var/ossec/etcdirectory by using following command.$ cd /var/ossec/etc - Open the
ossec.conffile and edit it based on your requirement.
Marketing Catalog Microservice
The Marketing Catalog Microservice is a comprehensive source of system-independent data of product details and marketing content crossing all the banks products, and capable of consuming products and services outside of the bank. Examples include products offered by FinTechs (such as payment devices) or real banking products that can be sold and marketed on behalf of other banks. Banks can choose to ingest the product details from the existing core or Product management system. This can be created and managed in the Marketing Catalog microservice.
- Run the installation on a fresh virtual machine.
IMPORTANT: If you execute the file on an existing virtual machine, ensure that Java is not installed. Otherwise, pointing it to Java 8 is mandatory.
- Create a cluster in your Atlas account and Allow access from anywhere in the IP access list. Then, create a database user for your cluster and connect it to your cluster. For the exact procedure that needs to be followed to execute this step, refer to Get Started with Atlas.
IMPORTANT: Ensure that you allow access from anywhere in the IP access list of the cluster. To do so, sign into your cluster and under Network Access go to IP Access List, click Edit, select Allow access from anywhere, and then save your changes.
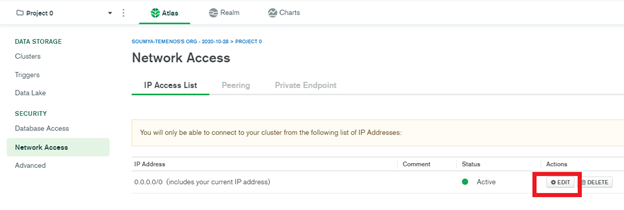
- Install MongoDB shell of the same version as the cluster version. If your cluster version is 4.2.10 (as displayed in the following image), then you must install MongoDB shell version 4.2.10.
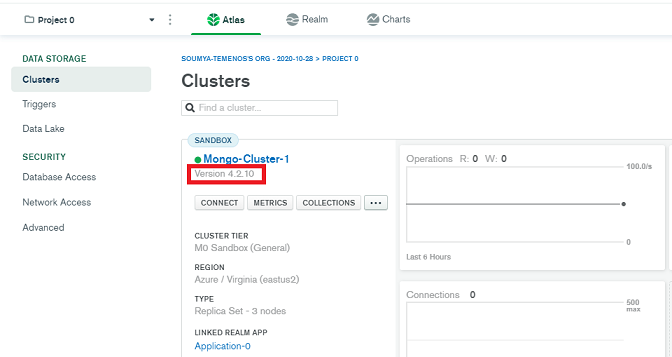
- To create the Marketing Catalog microservice resources along with the end to end installation of Quantum Fabric on Azure cloud, follow these steps:
- Provide the required inputs in the
conf/enterprise.propertiesfile. - Execute the
install-fabric.shfile.
- Provide the required inputs in the
- To create the Marketing Catalog microservice resources, follow these steps:
- From the
KonyFabricContainersAzure-_/lib/microservices/path, copy themarketing_catalogsfolder. - Provide the required inputs in the
conf/marketing_catalog_ms.propertiesfile. - From the
marketing_catalogsfolder, execute theinstall_marketing_catalog_ms.shfile.
- From the
Campaign Microservice
The Campaign microservice allows the branch user to create and store Campaign definition details.
- Run the installation on a fresh virtual machine.
IMPORTANT: If you execute the file on an existing virtual machine, ensure that Java is not installed. Otherwise, pointing it to Java 8 is mandatory.
- To create the Campaign microservice resources along with the end to end installation of Quantum Fabric on Azure cloud, follow these steps:
- Provide the required inputs in the
conf/enterprise.propertiesfile. - Execute the
install-fabric.shfile.
- Provide the required inputs in the
- To create the Campaign microservice resources, follow these steps:
- From
KonyFabricContainersAzure-_/lib/microservices/path, copy thecampaignsfolder. - Provide the required inputs in the
conf/campaign_ms.propertiesfile. - From the
campaignsfolder, execute theinstall_campaign_ms.shfile.
- From
