Support to MAP Public URLs - Reverse Proxy (on-premises)
In case of on-premises, if your Quantum Fabric is installed behind a reverse proxy and registered using a private URL or IP, you will need to expose identity and services end-points as public URLs. A reverse proxy is configured for exposing public URLs and then routing them to private Quantum Fabric URLs. When you create an Identity or Integration service, which is installed behind a reverse proxy, on Console, the service endpoints are exposed via intranet or private URLs during design time. You can access the service, however, via public URLs at runtime.
In some cases, there can be multiple reverse proxies depending on the region. For example, apps in Region1 may access Quantum Fabric via a reverse proxy in Region1, while the apps running in Region2 may access Quantum Fabric via a reverse proxy in Region2. In addition, the service endpoint URLs can be different when accessed from Region1 vs Region2.
To get the desired results from private and public URLs, you must modify the mapping selection from public URLs to private URLs in the identity server.
Sample Deployment Topology of Multiple Tenant URL Support in Identity Server
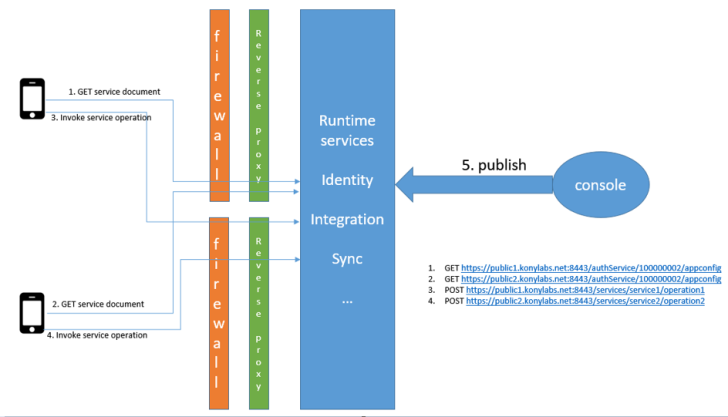
Public URL Mapping in Fabric User Interface (for On-premises only)
The Whitelisted Domain feature has been implemented to assist you in the process of mapping custom URLs for your Fabric services.
By using this feature, you can use public URLs to access Fabric in addition to private URLs. In some cases, private URLs (on which Fabric is originally installed) are restricted for internal access. In such cases, having public URLs will help client apps to access Fabric services. The User Interface (UI) access to this feature is supported from 202401 onwards.
NOTE: The feature is accessible via the API Management tab > API tab > Identity > Service Configuration.
NOTE: The UI is convince feature to set these values easily from the Identity Service Configuration page.
-
Log into your Fabric Console.
-
In the left-pane, click the API Management tab to display the services tabs such as APIs, Custom Code, and Custom Data Adapters.
By default the Identity service tab is selected under the APIs tab. -
In APIs > Identity page, click the SERVICE CONFIGURATION.
-
Under Whitelisted Domains, click the Add Domain.
-
In the Configure Domain dialog that appears, do the following:
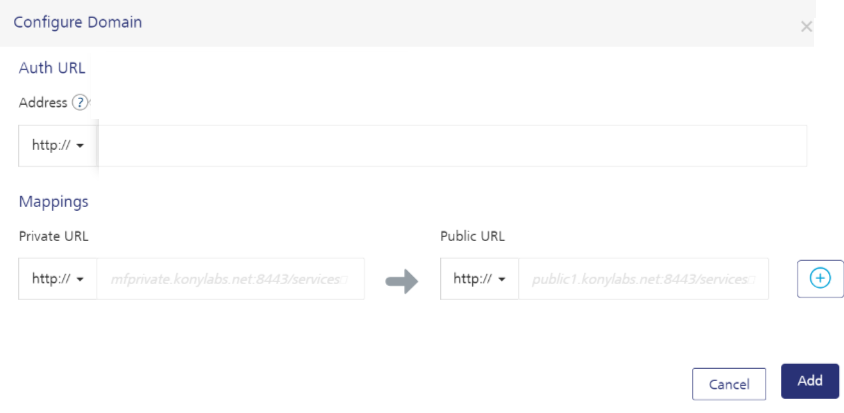
IMPORTANT: If you delete CUSTOM_TENANT_URLS property, Identity will be deleting CUSTOM_TENANT_SVC_URLS and CUSTOM_DOMAINS properties.
IMPORTANT: If you delete CUSTOM_TENANT_SVC_URLS property, Identity will be deleting CUSTOM_DOMAINS property.
-
In Auth URL, specify your custom identity provider URL. This URL will be used for authenticating users of your client app.
-
for example:
Auth URL for Identity Service:
//mfprivate.konylabs.net:8443/authService/api/v1/setup/tenants/accounts/properties
Auth URL for Fabric Back-end Services:
//mfprivate.konylabs.net:8443/authService/api/v1/setup/tenants/100000002/properties
-
-
In Mappings, you need to provide private and public service URLs.
-
Private URL: Private URL is the original URL on which a Fabric service is accessible. Private URLs may or may not be publicly accessible based on the Fabric installation.
NOTE: A Private URL is an Identity's endpoint during the Quantum Fabric setup. On-premises setups are usually private domain based URLs.
- Public URL: A client user uses a Public URL to access Fabric services. It is intended to be accessible publicly. Hence, a public domain used in the URL should already be reserved.
NOTE: Make sure to provide a clear and easy-to-understand URL that your clients can easily find and access.
NOTE: This is an outgoing request URL sent by public user.
For example:
Service URLs:
Private Service URL
Public Service URL
Sample1
"{\"https://public1.konylabs.net:8443/authService/100000002\": {\"https://mfprivate.konylabs.net:8443/services\": \"https://mfprivate.konylabs.net:8443/kpns\":Sample2
"{\"https://public1.konylabs.net:8443/authService/100000002\": \"https://mfprivate.konylabs.net:8443/kpns\":NOTE: These are the URLs of private domain services that have been associated with public service URLs.
Sample1
"{\"https://public1.konylabs.net:8443/authService/100000002\":
\"https://public1.konylabs.net:8443/services\", \"https://public1.konylabs.net:8443/kpns\"},Sample2
"{\"https://public1.konylabs.net:8443/authService/100000002\":
\"https://public1.konylabs.net:8443/kpns\"},NOTE: These are the official URLs for users to submit requests to the back-end services in the public domain.
-
-
API Commands to map Public URLs
The following is a sample code to map Identity public URLs (CUSTOM_TENANT_URLS).
POST https://mfprivate.konylabs.net:8443/authService/api/v1/setup/tenants/accounts/properties
With headers
X-Kony-Authorization: <auth token of admin>
Content-Type: application/json
Request payload:
{
"name": "CUSTOM_TENANT_URLS",
"value": "{\"https://public1.konylabs.net:8443/authService/accounts\": \"https://public1.konylabs.net:8443/authService/accounts\", \"https://public2.konylabs.net:8443/authService/accounts\": \"https://public2.konylabs.net:8443/authService/accounts\"}"
}
POST https://mfprivate.konylabs.net:8443/authService/api/v1/setup/tenants/100000002/properties
With headers
X-Kony-Authorization: <auth token of admin>
Content-Type: application/json
Request payload:
{
"name": "CUSTOM_TENANT_URLS",
"value": "{\"https://public1.konylabs.net:8443/authService/100000002\": \"https://public1.konylabs.net:8443/authService/100000002\", \"https://public2.konylabs.net:8443/authService/100000002\": \"https://public2.konylabs.net:8443/authService/100000002\"}"
}
The following is a sample code to map service URLs (CUSTOM_TENANT_SVC_URLS).
POST https://mfprivate.konylabs.net:8443/authService/api/v1/setup/tenants/100000002/properties
With headers
X-Kony-Authorization: <auth token of admin>
Content-Type: application/json
Request payload:
{
"name": "CUSTOM_TENANT_SVC_URLS",
"value": "{\"https://public1.konylabs.net:8443/authService/100000002\":{\"https://mfprivate.konylabs.net:8443/services\": \"https://public1.konylabs.net:8443/services\", \"https://mfprivate.konylabs.net:8443/kpns\": \"https://public1.konylabs.net:8443/kpns\"}, \"https://public2.konylabs.net:8443/authService/100000002\":{\"https://mfprivate.konylabs.net:8443/services\": \"https://public2.konylabs.net:8443/services\", \"https://mfprivate.konylabs.net:8443/kpns\": \"https://public2.konylabs.net:8443/kpns\"} }"
}
The following table details sample private and public URLs.
| URL | Type of URL |
|---|---|
https://mfprivate.konylabs.net:8443 |
Private URL |
https://public1.konylabs.net:8443 |
Public URL1 |
https://public2.konylabs.net:8443 |
Public URL 2 |
IMPORTANT: You must restart the Identity server after this configuration change.
