Infinity Spotlight Identity Service
Infinity Spotlight (formerly: Customer 360) Adapter is an identity connector that you can use in the Temenos Infinity application suite. This adapter supports multi-factor authentication (MFA) (if enabled), and it fetches profile and security attributes of users from the configured Infinity server.
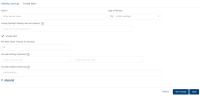
To configure an Identity service by using Infinity Spotlight adapter, follow these steps:
-
On the Identity service Design screen, in the Name box, type a name for the service.
-
From the Type of Identity list, select Infinity Spotlight.
-
In the Infinity Spotlight Identity Service Endpoint box, type the URL to which the Identity service must navigate to get the meta data.
-
The Enable MFA check box is selected by default. This helps you in the test login flow to test the status of the short-lived known_user token (whether it is issued or not). This setting has no impact on the Infinity server, as the server's adaptive algorithm decides the MFA status, and then responds accordingly in the login flow.
-
In the Pre-MFA Token Timeout (in Minutes) box, type the required value. It determines the timeout value for the short-lived known_user token.
-
In the Provider Settings (Optional) section, do the following:
-
In the Enter Parameter Key box, type the parameter that you want to configure as an additional attribute. For example,
<Backend-config-key>. -
In the Enter Parameter Valuebox, type the necessary parameter value. For example,
<backend-config-key-value>.
-
-
In the Provider Headers (Optional) section, type the header parameters from the login request.
-
In Advanced > Post Authentication URL, type the URL that you want to invoke after an Identity session is created. After this URL is invoked, the Identity response is returned to the client.
-
Click Test Login to verify the credentials. The Test Login dialog box appears.
-
Type the required details in the Header and Body boxes for the custom Identity provider.
-
The entries for the Header and Body boxes are auto-inserted to the login request. You can delete an entry by clicking the Delete beside it.
-
Click Sign In. The test results are displayed in the Identity Response dialog.
-
-
Click Save. Quantum Fabric displays the Identity screen, and the custom Identity service is configured.
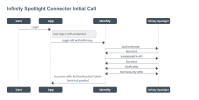
Initial Call Process by using Infinity Spotlight Adapter
When a user signs in to the Infinity application for the first time, the following calls occur among the Infinity app, Identity service, and Infinity server:
-
The login request is sent to the Quantum Fabric Identity service through the Login API.
-
The Identity service sends the login request to the Infinity server to be authenticated.
-
On successful authentication of the user from the Infinity server, the Identity service verifies the MFA status. By default, MFA is enabled. If MFA is not enabled, the Identity service returns the authenticated token.
-
If MFA is enabled, the Identity service sends a “known_user token” to the Infinity application.
-
The Infinity app contains the custom logic internal to its implementation to fetch MFA. The configured MFA can be of any type, namely: OTP, and/or security questions, and/or any custom logic to obtain an MFA key.
- OTP flow
-
If the bank or user enables OTP as the type of MFA, the Infinity app displays the OTP screen. And the app invokes a service that sends an OTP to the user's registered device.
-
After the user type the OTP, it is sent to the Infinity server to be validated.
-
On successful validation, the Infinity server sends an MFA key to the Infinity application.
-
The Infinity app sends the MFA key along with the Known User token to the Identity service.
-
- Security Questions Flow
-
If the bank or user enables Security Questions as the type of MFA, the Infinity app displays the Security Questions screen. And the app invokes a service that requests the Infinity server to send the security questions.
-
After the user provides the answers to the questions, they are sent to the Infinity server to be validated.
-
On successful validation, the Infinity server sends an MFA key to the Infinity application.
-
The Infinity app sends the MFA key along with the Known User token to the Identity service.
-
-
The Identity service sends the MFA key and the Known User token to the Infinity server to validate the user who is trying to access the Infinity application.
- On successful validation, the Infinity server sends the profile and security attributes of the user to the Identity service.
-
The Identity service sends the authenticated token with full profile details to the Infinity application.
Subsequent Call Process by using Infinity Spotlight Connector
On subsequent logins, the following calls occur among the Infinity app, Identity service, and Infinity server:
-
The Infinity application invokes the Login API along with the stored MFA key, and sends the details to the Identity service.
-
The Identity service sends the MFA key and the known_user token to the Infinity server to validate the user who is trying to access the Infinity application.
-
On successful validation, the Infinity server sends the profile and security attributes of the user to the Identity service.
-
The Identity service sends the authenticated token with full profile details to the Infinity application.
IMPORTANT: This document contains the information about the intended implementation for the connector. As the actual implementation can vary, kindly refer the Infinity documentation (Infinity > Digital Banking Platform > Feature Description and Specification - Digital Banking Platform > Infrastructure Services > Local Services > Local Services - API Reference > Login Local Services > dbxUserLogin (Orchestration Service)) to know the actual implementation.
SDKs
NOTE: These APIs are valid from V8 SP4 Fix Pack 14 onwards.
getMfaDetails
The getMfaDetails function helps you to identify whether multi factor authentication (MFA) is enabled or disabled in the Identity service. If MFA is enabled, this function also lets you know the type of MFA that is active.
Signature
<IdentityObj>.getMfaDetails()
Parameters
None
Return Type
JSON - containing enablement flag and metadata
Example
var serviceName = "identity_service_name";
// Get an instance of SDK
var client = kony.sdk.getCurrentInstance();
var identitySvc = client.getIdentityService(serviceName);
var mfaDetails = identitySvc.getMfaDetails();
if(mfaDetails["is_mfa_enabled"] == true){
kony.print(“mfa is enabled and mfa meta information is -“+JSON.stringify(mfaDetails["mfa_meta"]));
}
validateMfa
The validateMfa function validates the MFA parameters. On successful validation, this function allows you to access the client use cases that were restricted which were restricted by multi-factor authentication.
Signature
< IdentityObj >.validateMfa(mfaParams , successCallback, errorCallback)
Parameters
| Parameter | Type | Description | Required |
|---|---|---|---|
| mfaParams | JSON |
These parameters must match with the getMfaDetails() response parameters. |
Yes |
| successCallback | Function | This function is invoked on successful MFA validation. | Yes |
| errorCallback | Function | This function is invoked when there is an error while MFA validation with the cause of failure as an argument. | Yes |
Return Type
None
Example
var serviceName = "identity_service_name";
// Get an instance of SDK
var client = kony.sdk.getCurrentInstance();
var identitySvc = client.getIdentityService(serviceName);
var mfaParams = {"mfa_Key" : "mfa value"};
function successCallback(){
kony.print("validation successful");
}
function errorCallback(err){
kony.print("validation unsuccessful with error - "+ JSON.stringify(err));
}
identitySvc.validateMfa(mfaParams , successCallback, errorCallback);