Post-Installation Tasks
Configuring Secure Sockets Layer (SSL) Certificate
You can troubleshoot trusted certification issues.
IMPORTANT: Apple's App Transport Security (ATS) mandates HTTPS for all communication and requires the use of TLS v1.2 or higher for all SSL certificates and load balancers.
For Apple apps to work properly and adhere to App Store guidelines, you must enable your Quantum Fabric on-premises instance with SSL and configure your network infrastructure to use TLS version 1.2 or higher. For more information, please refer to the following: Temenos Basecamp article on ATS Compliance.
After installing Quantum Fabric on HTTPS, import your SSL certificate (for example, domain.subdomain.crt) into your Quantum Fabric Installer's JRE trusted certificate authority (CA) certificates file - for example, <INSTALL_DIR>/jre/lib/security/cacerts
If your SSL certificate is not configured, the system displays an error - "peer not authenticated". For details, refer to Troubleshoot with SSL Certificate Issues.
To enable communication between Quantum Fabric Console and other products such as Quantum Fabric Integration Services, and Quantum Fabric Engagement Services, follow these steps:
- import each product's certificate (Quantum Fabric Integration Services, and Quantum Fabric Engagement Services) into the Quantum Fabric console (for example,
<INSTALL_DIR>/jre/lib/security/cacerts). - import console cert into the product boxes cacerts such as Quantum Fabric Integration, Quantum Fabric Engagement Services, and Quantum Fabric Management.
Add an Installer Generated Self-Signed SSL Certificate to Cacerts
To add an installer generated self-signed SSL certificate to cacerts, follow these steps:
- From your Quantum Fabric installed system, open the Linux terminal, and run the following command to generate an
intermediate.crtfile from the keystore:<USERINSTALLDIR>/jre/bin/keytool -export -alias "<HOST_URL_SSL_CONF>" -file <USERINSTALLDIR>/intermediate.crt -keystore <USERINSTALLDIR>/keystore.jks -storepass <Passsword_of_keystore>
Based on the hostname and keystore password provided at the SSL Certificate window, the preceding command exports the required certificate from the source keystore with the given name - for example,
intermediate.crt. -
Run the following command to import the
intermediate.crtcertificate file into your Quantum Fabric Installer's JRE trusted certificate authority (CA) certificates file:<USERINSTALLDIR>/jre/bin/keytool -import -noprompt -trustcacerts -alias "<HOST_URL_SSL_CONF>" -file <USERINSTALLDIR>/intermediate.crt -keystore <USERINSTALLDIR>/jre/lib/security/cacerts -storepass changeit
Add an Existing SSL Certificate to Cacerts
If Java does not identify a certificate issuer by default, you need to import an SSL into your cacerts.
To add an existing SSL certificate to cacerts, follow these steps:
Use the following steps to import your existing certificate to cacerts with the proper value of alias, keystore location and keystore password.
- From your Quantum Fabric installed system, open the Linux terminal, and run the following command to add an
intermediate.crtfile from the keystore:<USERINSTALLDIR>/jre/bin/keytool -export -alias "<yourcertificate_domain>" -file <USERINSTALLDIR>/intermediate.crt -keystore <keystore_location>-storepass <Passsword_of_keystore>
- Run the below command to import the
intermediate.crtcertificate file into your Quantum Fabric Installer's JRE trusted certificate authority (CA) certificates file:<USERINSTALLDIR>/jre/bin/keytool -import -noprompt -trustcacerts -alias "<yourcertificate_domain>" -file <USERINSTALLDIR>/intermediate.crt -keystore <USERINSTALLDIR>/jre/lib/security/cacerts -storepass changeit
JDK Version Compatibility
In case if you upgrade your JDK version in your middleware server, to enable JDK version compatibility, make the appropriate changes in an app server's middleware.properties file located in your middleware server installation folder.
For example: When you upgrade JDK V 1.6 to JDK V 1.7 (vice-versa), you can still run your middleware server. Quantum Fabric's run-time apps cannot be accessed. If you try to access any apps at runtime, the system throws an error message due to JDK version incompatibility.
- In your middleware server installation folder, open the
middleware.propertiesfile located at the below path:- for JBoss:
<installer folder>\middleware_home\middleware\middleware-bootconfig - for Tomcat:
<installer folder>\middleware_home\middleware\middleware-bootconfig
- for JBoss:
-
Make the following changes in the
middleware.propertiesfile.ssl.trustStore=/<java_home>/jre/lib/security/cacertsssl.keyStore=/<java_home>/jre/lib/security/cacerts
Configure Memcache for Integration Services
For Quantum Fabric, you can configure the memcache from the Admin console.
To configure memcache in Quantum Fabric, follow these steps:
- Open Admin console (http/https://<server-host>:<server-port>/admin).
- In the left pane, go to the Settings tab.
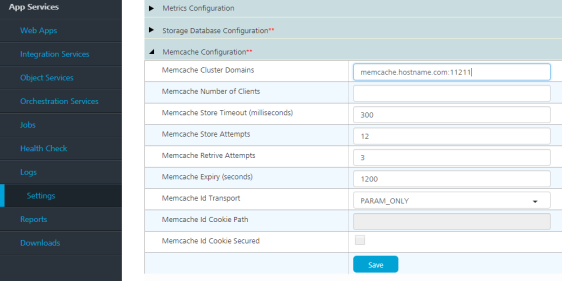
- Under the Runtime Configuration tab, expand the Memcache Configuration key.
- In the Memcache Cluster field, provide your memcache hostname/IP and port details separated with a colon. For example, <hostname/IP>:<Port>
- Save the changes.
mbaasportal.war Deployment for Multi-Node Installations
Once Quantum Fabric installation succeeds, the Quantum Fabric Console will not be displayed as the enable-welcome-root value is set true in thedomain.xml file.
To configure mbaasportal.war, follow these steps:
- In the master node, open the
domain.xmlfile fromJBOSSDIR/domain/configuration, and search for enable-welcome-root="true." - Replace enable-welcome-root="true" with enable-welcome-root="false."
Remote Installation Prerequisites
After you have installed Quantum Fabric, you must retain the Installation folder for upgrades. While upgrading, the Quantum Fabric installer requires the installvariables.properties file under the <USER_INSTALL_DIR>/_Quantum Fabric_installation folder.
Installing Quantum Fabric Remotely
You can install Quantum Fabric remotely on the following supported application servers:
- JBoss Multi-node
- JBoss Standalone pre-existing
- WebLogic
Disable Sending of Usage Data Anonymously
Allows Temenos to collect product usage information to make your Quantum Fabric experience better.
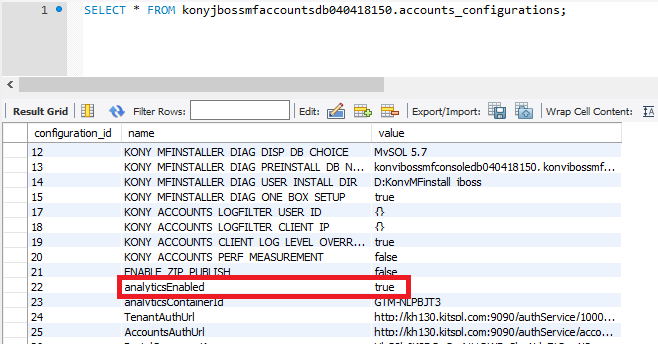
- Go to the Accounts database configured for the Quantum Fabric installation.
- Open the account_configurations table.
- Find the row entry in the name column with name as
analyticsEnabled. - Modify it to true/false.
- Refresh Quantum Fabric Console.
You should be able to figure out if analytics data that is sent/out by trying to check in the Network tab in the Browser Developer Tools.
Performance Improvements for JBoss (Pre-existing and Domain Mode)
While using pre-configured JBoss or JBoss in Domain Mode, add the following snippet to the datasource to improve the performance.
<pool>
<min-pool-size>10</min-pool-size>
<max-pool-size>30</max-pool-size>
<flush-strategy>IdleConnections</flush-strategy>
</pool>
NOTE: For the bundled version, the installer will add the default size to the datasources.
Health Check URL
The following is the Component Health Check URL if the initial setup is success:
<http/https>://<Domainname>:<port>/mfconsole/health_check/all
{"workspace":"passed","accounts":"passed","portal":"passed"}
<http/https>://<Domainname>:<port>/authService/v1/manage/checkhealth
Passed
<http/https>://<Domainname>:<port>/admin/healthcheck?output=json
{"healthCheck":"PASSED","healthDetail":
{"Access to Reporting Queue":"PASSED","Access to Admin DB":"PASSED","Access to Reports DB":"PASSED","Access to Storage DB":"PASSED"}
,"version":"V8 SP2 FP1 HF1"}
<http/https>://<Domainname>:<port>/services/healthcheck?output=json
{"healthDetail":
{"appID":"services","Access to Reporting Queue":"PASSED","Access to Admin DB":"PASSED","Access to Storage DB":"PASSED"}
,"applicationHealthCheck":"PASSED","version":{"Middleware Version":"KonyFabricInstaller-GA-8.2.1.1"}}
<http/https>://<Domainname>:<port>/kpns/service/healthcheck/json
{"healthCheck":"PASSED","healthDetail":
{"Quartz jobs":"PASSED","Access to Database Server":"PASSED","Security Credentials":"PASSED"}
,"version":"8.2.1.1_GA"}
Steps to enable SAPJCo
The installer provides the following artifacts:
- SapJCoDestinationProvider.jar
- Module.xml (for JBoss)
You can download the other artifacts libsapjco3.so (for Linux) or sapjco3.dll (for Windows), and sapjco3.jar from https://websmp204.sap-ag.de/connectors.
The SapJCoDestinationProvider.jar can be located at:
<USER_INSTALL_DIR>/Integration/sapjco/main- for JBoss
The Module.xml can be located at:
<USER_INSTALL_DIR>/Integration/sapjco/main
Steps for Tomcat
- Navigate to
<USER_INSTALL_DIR>/tomcat/lib, and add the following files:- sapjco3.jar
- libsapjco3.so/sapjco3.dll
NOTE: The SapJCoDestinationProvider.jar is already placed in the
<USER_INSTALL_DIR>/tomcat/libby the installer. - Restart the server
Steps for JBoss
For Windows: Place the sapjco3.dll in the jboss/bin folder or C:/Users/<USER_NAME>/System32 folder.
For Linux: Place the libsapjco3.so in the /usr/bin folder or any location on the machine and append the path to the $LD_LIBRARY_PATH variable
JBoss - Standalone (Bundled)
- Navigate to
<USER_INSTALL_DIR>/jboss/modules/org/sapjco/main, and add the following files:- sapjco3.jar
- SapJCoDestinationProvider.jar
- Navigate to
<USER_INSTALL_DIR>/jboss/modules/org/sapjco/main/- In
module.xml, under the <resources> tag add<resource-root path="sapjco3.jar"/>. - In
standalone-full.xml, under the <global-modules> tag add<module name="org.sapjco" slot="main"/>.
- In
JBoss - Standalone(Pre-configured)/Domain mode
- Navigate to
<JBOSS_DIR>/modules/org/sapjco/main, and add the following files:- sapjco3.jar
- SapJCoDestinationProvider.jar
- Navigate to
<JBOSS_DIR>/modules/org/sapjco/main.- In
module.xml, under the <resources> tag add<resource-root path="sapjco3.jar"/>. - In
standalone.xmlordomain.xml, in the subsystem add<subsystem xmlns="urn:jboss:domain:ee:4.0">. Add the following tag:
- In
<global-modules>
<module name="org.sapjco" slot="main"/>
</global-modules>
Steps for Weblogic
- Navigate to
<WL_HOME>/wlserver/server/lib, and add the following files:- sapjco3.jar
- SapJCoDestinationProvider.jar
- libsapjco3.so/sapjco3.dll
-
Go to
<WL_HOME>/user_projects/domains/base_domain/bin, and edit the startWeblogic script file using one of the following commands.- For Windows:
startWeblogic.cmd - For Linux:
startWeblogic.sh
- For Windows:
-
Prepend your JAR files to the SAVE_CLASSPATH environment variable.
For example, in startWeblogic.sh add:
SAVE_CLASSPATH="${WL_HOME}/server/lib/SapJCoDestinationProvider.jar:${WL_HOME}/server/lib/sapjco3.jar:${WL_HOME}/server/lib/libsapjco3.so:${CLASSPATH}". - Restart the server.
